microsoft cloud app security best practices
For instance if you havent seen the following pages on Power Platform Guidance ALM and Administration theyre great and suggest going through them. Theyve been pointing out that the cloud proved beneficial for the.

Using Microsoft Defender For Cloud Apps Controls In Power Bi Power Bi Microsoft Docs
The service is frequently degraded and one of their support engineers told us thats normal Features which should be there -- like actual checkboxes -- are missing from our instance.

. A successful digital transformation requires weaving together technology data process and operational change. Microsoft highly recommends that Identity be centralized into a single Authoritative source. APIs and Best Security Practices for Microsoft Defender for Cloud Apps update.
Microsoft Azure is the cornerstone of cloud infrastructure for many enterprises across the globe. Microsoft 365 Security Best Practices Keeping Your Work and Documents Safe in 2022. The Microsoft 365 formerly Office 365 suite of cloud-based services has its challenges in the name of misconfigurations and security weaknesses.
Microsoft Defender for Cloud provides you the tools needed to harden your network secure your services and make sure youre on top of your security posture. The articles below contain security best practices to use when youre designing deploying and managing your cloud solutions by using Azure. Building on that we are introducing the ability to export usage telemetry to Azure Data Lake.
Office 365 SharePoint Online. Once custom apps are configured you see information about whos using them the IP addresses they are being used from and how much traffic is coming into and out of the app. The Cloud app catalog is an important part of cloud app security.
These best practices come from our experience with Azure security and the experiences of customers like you. Expand your cloud business. Learn how to keep data safer in the cloud with these five best practices from Microsoft security experts.
To gain additional visibility into activities from your line-of-business apps you can onboard custom apps to Defender for Cloud Apps. These four domains have one thing. Crafted from the insights and best practices of over 1000 Microsoft partners.
Wow does it look good in the marketing materials. Get a step-by-step walkthrough with this infographic and discover how to. If one of these domains fails to make the grade your entire transformation may be in jeopardy.
It provides a comprehensive solution to give organizations improved visibility into cloud activities uncover shadow IT assess risks enforce polices investigate suspicious activities and stop threats. Implement security best practices is the largest control that includes more than 50 recommendations covering resources in Azure AWS GCP and on-premises. Reduce problem areas with tools for identifying different.
Many users casually grant OAuth permissions to third-party apps to access their account information and in doing so inadvertently also give access to their data in other cloud appsUsually IT has no visibility into these apps making it difficult to weigh the security risk of an app against the. Its important to know how to utilize APIs in order to work with a CASB like Microsoft Defender for Cloud Apps. Microsoft Docs is often the first go to place if we want to get How Tos and more information on best practices.
Microsoft 365 provides powerful online cloud services that enable collaboration security and compliance mobility intelligence and analytics. Read on as through this article we share some of cloud application security best practices and associated checklists that can help keep your cloud environment secure. The Cloud Practice Development Playbooks provide the essential blueprints and tools to develop analyze manage and secure an effective cloud practice thats built to last.
Mission-critical workloads ranging from distributed Kubernetes clusters to NET applications to Software-as. CIS is a nonprofit entity focused on developing global standards and recognized best practices for securing IT systems and data against the most pervasive attacks. By Omri Amdursky Microsoft Defender for Cloud Apps.
Shift how you think about data protection to include cloud security. What it does is rate the different risks for your cloud apps. Five Best Practices for Cloud Security.
Manage OAuth apps that are authorized by your users Detail. Onboard custom apps Detail. Access current Microsoft Defender for Cloud best practices for securing apps so you know exactly what steps we recommend and implement with the same toolkit we use to secure our own apps.
Microsoft Azure Security Best Practices. For almost a decade IT professionals have been encouraging companies to move to the cloud. Putting APIs in the forefront of security practices.
Were doing a proof-of-concept demo of Microsoft Cloud App Security. Moreover organizations using Microsoft Cloud App Security today administrators can monitor Power BI reports for suspicious access patterns and alerts to take timely actions. As Microsoft Azure relies on Azure Active Directory for authentication these Azure Security best practices are also critical to the security of your Azure cloud.
By Safiyyah OQuinn Product Marketing Manager Dynamics 365 Field Service. Cloud Security Gateways Q2 2021. Ann Johnson CVP of Cybersecurity Solutions Group at Microsoft kicked off the.
Microsoft cloud app security or CASB is a critical component of the Microsoft cloud security stack. Many of the same cloud security fundamentals we discussed previously also apply to other cloud environments so were going to use that best practice cloud security knowledge we learned in the last blog and apply it to Microsoft Azure. The best practices are intended to be a resource for IT pros.
To ensure the cloud app catalog is kept up to date there are several processes that are run within it. It helps protect cloud-based apps data and infrastructure with the right combination of well-defined models processes controls and policies. This article offers 12 Microsoft 365 security best practices for enterprise IT pros to make.
March 3 2022 5 min read. Your guides to cloud business transformation. The risk rating assigned to an app is based on regulatory certification industry standards and best practices.
We launched the Azure Security Expert Series which is will provide on-going virtual content to help security professionals protect hybrid cloud environments. In a hybrid identity scenario an Azure Security best practice is to integrate your on. Microsoft Defender for Cloud Apps is named a Leader in The Forrester Wave.
Trend Micro Conformity highlights violations of AWS and Azure best practices delivering over 750 different checks across all key areas security reliability cost optimisation performance efficiency operational excellence in one easy-to-use package.

Application Security In Azure Microsoft Docs

A Better Cloud Access Security Broker Securing Your Saas Cloud Apps And Services With Microsoft Cloud App Security Microsoft Security Blog

Integrate Azure Active Directory Identity Protection With Defender For Cloud Apps Microsoft Docs
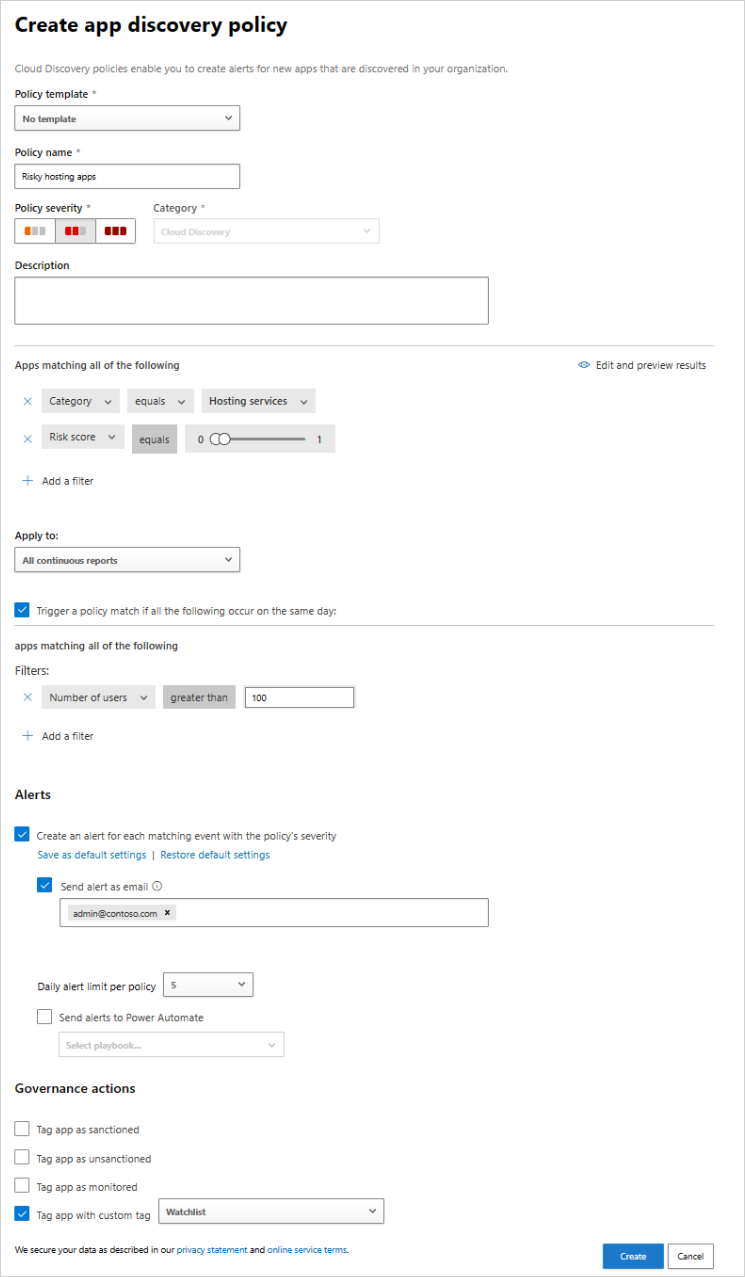
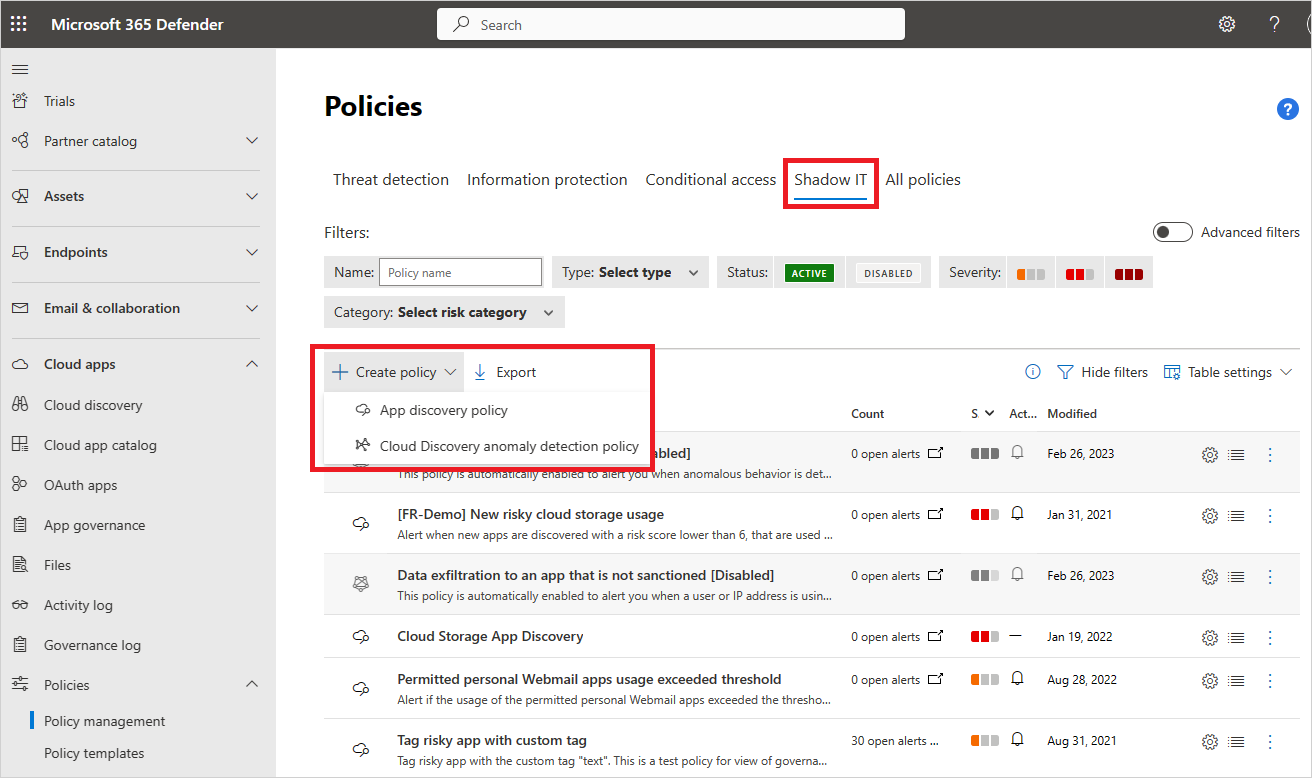
Create Policies On Cloud Discovery Apps Microsoft Docs

Connect Office 365 To Defender For Cloud Apps Microsoft Docs

Using Microsoft Defender For Cloud Apps Controls In Power Bi Power Bi Microsoft Docs

Microsoft Defender For Cloud Apps Securite Des Casb Securite Microsoft
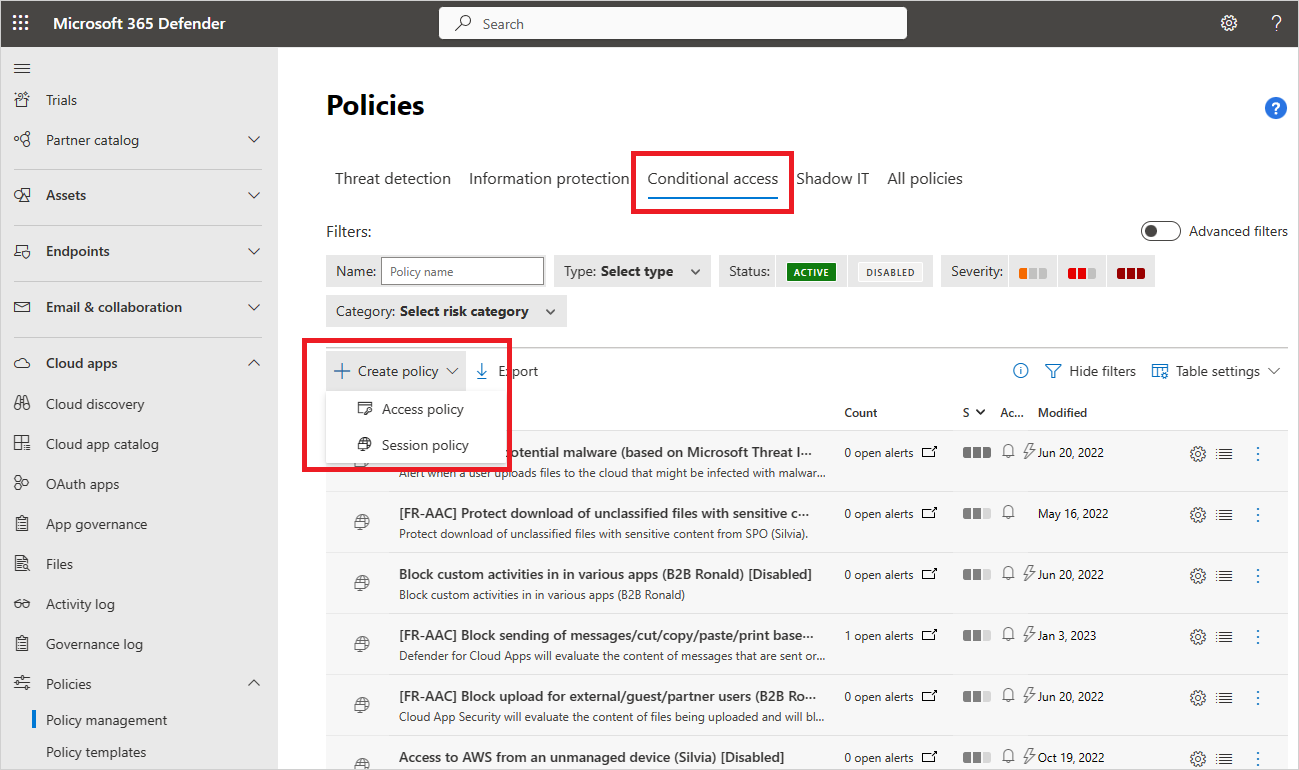
Create Session Policies In Defender For Cloud Apps Microsoft Docs

Microsoft Security Best Practices Microsoft Docs

Connect Office 365 To Defender For Cloud Apps Microsoft Docs

Using Microsoft Defender For Cloud Apps Controls In Power Bi Power Bi Microsoft Docs

Using Microsoft Defender For Cloud Apps Controls In Power Bi Power Bi Microsoft Docs
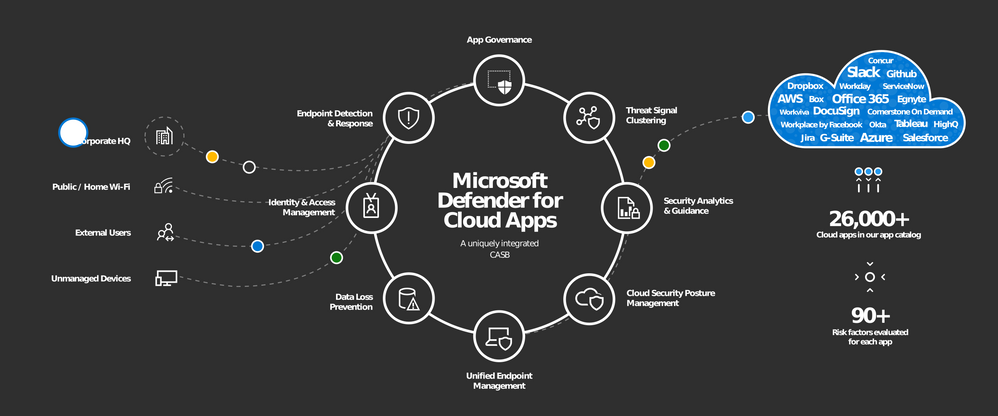
Introducing Microsoft Defender For Cloud Apps

Recommended Microsoft Defender For Cloud Apps Policies For Saas Apps Microsoft 365 Enterprise Office 365 Microsoft Docs

Protect Active Directory With Microsoft Defender For Identity 4sysops
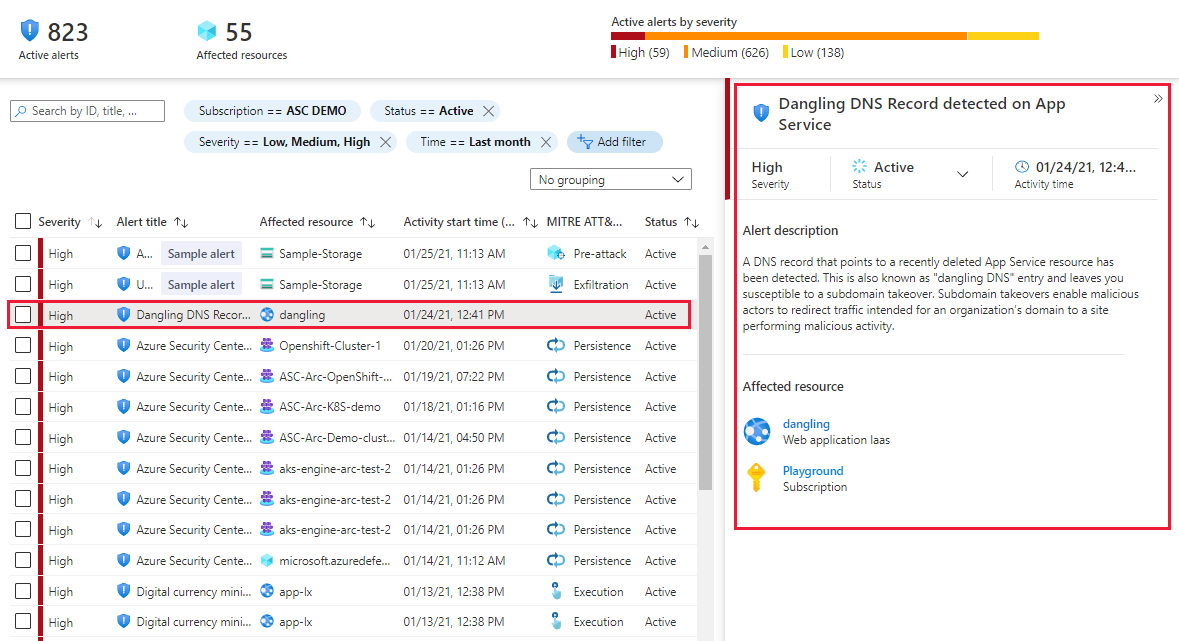
Microsoft Defender For App Service The Benefits And Features Microsoft Docs
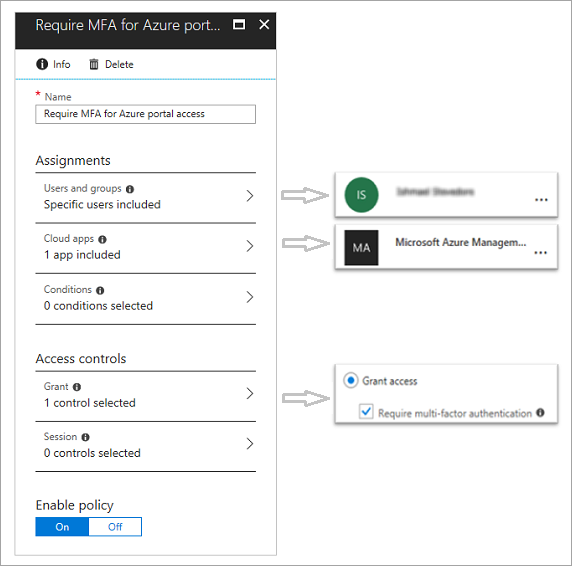
Recommendations For Conditional Access And Multi Factor Authentication In Microsoft Flow
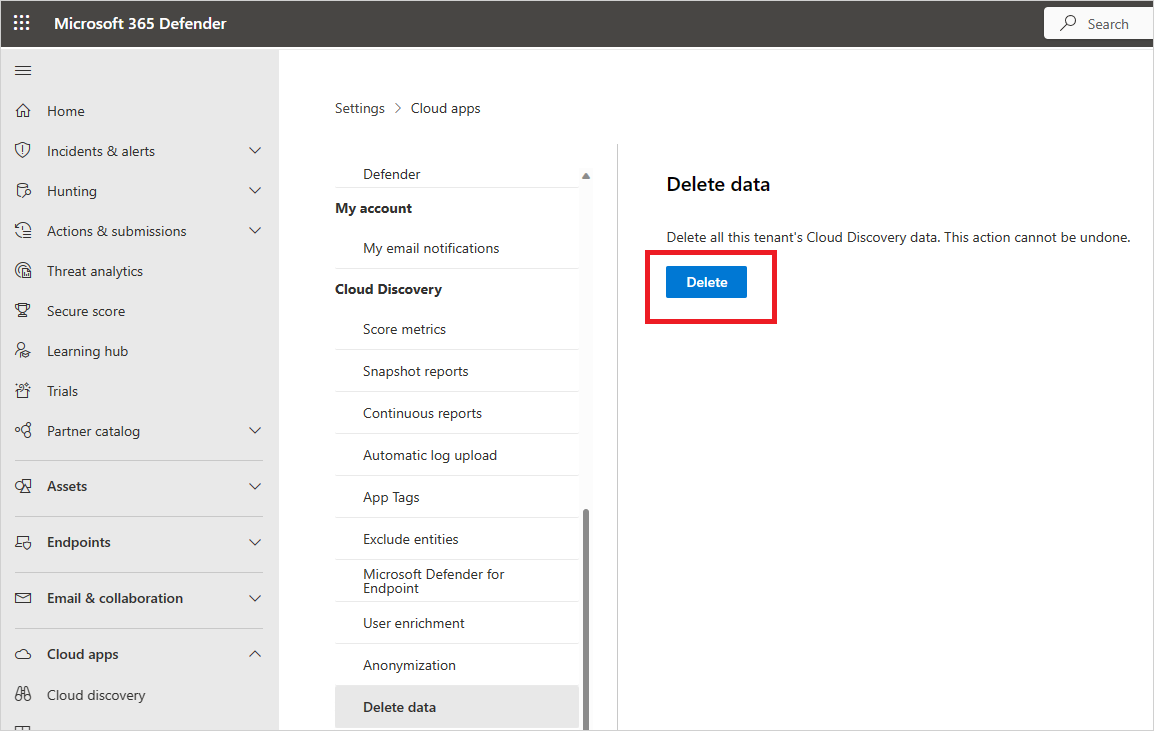
Use Cloud Discovery Data To Detect Risky Behavior Microsoft Docs